Internet is the global meeting place for personal and business communication. Internet has transformed enterprise networks to achieve business outcomes, while unintentionally exposing them to new vulnerabilities leading to - loss of employee productivity, data leakage, bandwidth drainage, legal liability for unsafe surfing etc.
Network Security & Next Gen. Firewall
It works as security gateway between intranet & internet and enforces network access & security policies among all the users in organization. Properly configured firewall can replace many legacy servers like proxy, DNS, DHCP, RADIUS, link load balancer etc. A stateful Packet inspection(SPI) firewall is a network security device that filters incoming and outgoing network traffic based upon Internet Protocol (IP) port and IP addresses.
A next generation firewall (NGFW) combines traditional firewall technology with additional functionalities such as encrypted traffic inspection, deep packet inspection (DPI), gateway anti virus, application control, intrusion prevention (IPS) and advanced threat prevention (ATP) capabilities like Sandboxing.
User identity based technology allows administrator to create internet access policies based on user, group or department. User authentication can be performed using local user database, RADIUS, LDAP, Active Directory or any combination of these. It provides granular control in dynamic IP environments like DHCP & Wi-Fi where the users can’t be identified through IP addresses.
NAT firewalls allow multiple devices with independent network addresses to connect to the internet using a single IP address, keeping individual IP addresses hidden. NAT firewalls are similar to proxy firewalls in that they act as an intermediary between a group of computers and outside traffic.
Proxy server provides caching and access control for HTTP request, effectively speeding up services and saving time. Firewall configured as Web Proxy – filters network traffic at the application level. Web Proxy enforces Web and Application Filter policy and Anti Virus policy as configured in User and Firewall Rule.
Domain Name System (DNS) helps users find Internet applications, computers, or other network devices by translating domain names into IP addresses.
DHCP server is responsible for assigning the IP Address to the client and for keeping a record of all clients and the IP Address assigned to them.
IPS (Intrusion Protection System) is a form of network security that works to detect and prevent identified threats. It continuously monitors your network, looking for possible malicious incidents and capturing information about them.
OEMs: Sophos, Barracuda, GFI
SD-WAN
As the use of business-critical, cloud-based applications and tools continue to increase, distributed organizations with multiple remote offices are switching from performance-inhibited wide-area networks (WANs) to software-defined WAN (SD-WAN) architectures. However, SD-WAN has its own shortcomings—especially when it comes to security with direct internet access. SD-WAN includes next-generation firewall (NGFW) security, SD-WAN, advanced routing, and WAN optimization capabilities.
SaaS applications like Office 365, G-Suite increase overall traffic while requiring very low latency to work. To manage these demands, you need a different architecture that enables local internet breakouts at every location for direct access to cloud services. The current scenario of Hybrid WAN (Internet and MPLS ) is challenged by an intelligent SD-WAN technology that provides better features and performance.
SD-WAN mainly deals with
- WAN links
- Branch office connectivity
- VPN support & orchestration
- Application visibility & routing
Software-Defined Wide-Area-Network(SD-WAN) is an increasingly popular and cost-effective alternative to dedicated network connections and MPLS infrastructures. SD-WAN significantly increases WAN network reliability, agility, and performance by using and aggregating multiple active, load-sharing connections of any type (Broadband/cable, MPLS, 3G/4G).
Advanced data caching, traffic compression, and other WAN optimization capabilities leverage the available bandwidth. This lets you ensure that there is always enough bandwidth for business-critical applications, by automatically making dynamic, on-the-fly adjustments to QoS and application usage policies depending on real-time bandwidth and latency measurements.
Key components of SD-WAN include:
- Ability to route traffic over your existing network connections with support for multiple network technologies including MPLS, Internet broadband, fiber, LTE, and DSL.
- Automatic failover of network connections.
- Ability to dynamically change network paths to optimize network traffic loads.
- Segmentation to automatically priority and route network traffic based on its source or type.
- A visual management console that lets administrators manage the network from a central location without dealing with physical network connections.
- Zero-touch provisioning of new branches and locations.
- Support for VPNs.
Benefits of SD-WAN:
- Lower costs by replacing expensive ILL & MPLS connections with cost-effective broadband options such as Ethernet, DSL and 3G/4G
- Achieve consistent performance and availability of business-critical and SaaS applications
- Secure traffic from advanced threats across the entire network
- Simplify deployment and ongoing management through centralized administration
OEMs: Sophos, Barracuda, GFI
UTM & Internet Security
 Firewall is no longer sufficient to protect an enterprise network, as apart from external blended network attacks, enterprises increasingly face serious threats from insiders.
Firewall is no longer sufficient to protect an enterprise network, as apart from external blended network attacks, enterprises increasingly face serious threats from insiders.
The growth of UTM (Unified Threat Management) is a witness of logical evolution where various segregated solutions like gateway AntiVirus, inbound and outbound Spam, Content Filtering, URL filtering etc have emerged together in a single platform with a user-friendly interface and manageability.
OEMs: Sophos (Cyberoam), Barracuda, CheckPoint
Email Security
Email has become the de facto medium through which organisations carry out their business communication and share important data. The ever-growing popularity has also enabled hackers to use email as an attack vector. As per the statistics, 91% of cyber attacks start with an email. Incoming and outgoing email can expose your organization to viruses, spam, confidential data loss, regulatory violations or legal disputes.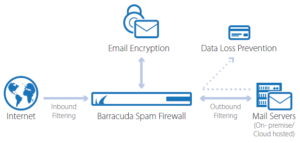
Over the past few years, phishing emails continue to exploit even the most experienced professionals. This is because the attachments in these emails are designed to look legitimate and prod an individual to click on them. Phishing emails can also trick a person into sharing sensitive information by posing as a trusted individual or organization.
The malware sent through email attacks can bring down the reputation of your company to an end. Spam mails not only expose your network to email-borne threats such as phishing, malware and ransomware, but also consumes lot of internet bandwidth and disk space of your desktop/laptop and on premise mail server.
Inbound anti spam gateway solutions have Recipient Verification and Sender Policy Framework tools to enhance email security. An outbound secure email gateway allocates a Spam Confidence Score to each outbound email and inspects it for malware. This process prevents a business´s IP address being blacklisted by global block list agencies. On-premise anti spam solutions can be more customizable than cloud-based solutions.
Secure Email Gateways, provide pre-delivery protection by blocking email based threats, whether on-premise or cloud based mail solutions like Office 365 / G-Suite. They protect businesses from spam, viruses, malware and denial of service(DoS) attacks. The gateway scans all inbound, outbound and internal email communications, including attachments and URLs for signs of malicious or harmful content.
OEMs: Sophos, Barracuda, GFI
Web Application Firewall
In business- employees, customers, suppliers and partners connect and get their  job done through applications like email, erp, crm, scm, hrm, payroll etc. These applications are run on web servers and need to be delivered securely over HTTPS to provide access to its onsite and offsite users through authentication process.
job done through applications like email, erp, crm, scm, hrm, payroll etc. These applications are run on web servers and need to be delivered securely over HTTPS to provide access to its onsite and offsite users through authentication process.
A WAF protects your web based applications by filtering, monitoring, and blocking any malicious HTTP/S traffic traveling to the web application, and prevents any unauthorized data from leaving the app. It does this using reverse proxy policy and acting as an intermediary that protects the web app server from a potentially malicious client. Web Application Firewall helps you enable HTTPS quickly and easily, even for legacy applications, with Instant SSL capabilities.
WAF provides a central point of control, helps ensure up-to-date policies, and provides the tools necessary to deliver ongoing security for your applications wherever they reside. Furthermore, role-based access control enables you to manage security at every stage of the application lifecycle with simplicity.
OEMs: Sophos, Barracuda, Checkpoint
VPN & Remote Access
VPNs are used by businesses to extend private networks over the public internet, allowing remote workers or offices to connect to a company’s LAN and its centralised resources . Initially, two basic VPN types were used to achieve this networking solution: Remote-Access VPN and Site-to-Site VPN.
Site to site VPN:
IPSec based VPNs create a tunnel between two network and provide direct (non-proxied) access and full visibility to the entire network. IPSec needs compatible VPN gateway at both locations to protect from hackers who can use the remote IPSec VPN tunnel to gain unauthorized access to the corporate network. VPN gateways are in charge of authentication of the user and the network, encryption, and the integrity of the data.
Intranet-based site-to-site VPNs are used to combine the LANs of multiple office locations into one single private network., which would then be known as a WAN (Wide Area Network). Extranet-based site-to-site VPNs, on the other hand, allow your company to use the public internet to connect its LAN with those of other companies, customers, or communities.
 L2TP or Layer 2 Tunneling Protocol is the result of a partnership between Cisco and Microsoft. It was created to provide a more secure VPN protocol than PPTP. L2TP uses 256 bit keys giving a higher level of encryption. It uses the IPSec suite to provide end-to-end encryption, data origin authentication, replay protection, as well as data integrity. L2TP VPN is a combined protocol that has all the features of PPTP, but runs over a faster transport protocol (UDP) thus making it more firewall friendly.
L2TP or Layer 2 Tunneling Protocol is the result of a partnership between Cisco and Microsoft. It was created to provide a more secure VPN protocol than PPTP. L2TP uses 256 bit keys giving a higher level of encryption. It uses the IPSec suite to provide end-to-end encryption, data origin authentication, replay protection, as well as data integrity. L2TP VPN is a combined protocol that has all the features of PPTP, but runs over a faster transport protocol (UDP) thus making it more firewall friendly.
Remote access VPN
SSL VPNs are designed specifically to enable increased productivity for remote users by providing easy-to-use, secure remote access to applications. SSL works at the application layer instead of the network layer, providing the highly granular policy and access control needed for secure remote access. Because SSL is included in all modern browsers, SSL VPNs can empower today’s mobile workforce with clientless remote access. A remote-access VPN requires a VPN gateway, to encrypt/ decrypt the outgoing/incoming traffic, authenticate the credentials of any device attempting to sign into the VPN.
PPTP (Point-to-Point Tunneling Protocol) VPN developed by Microsoft uses 128-bit encryption which makes it the fastest but the weakest in terms of security. PPTP is supported on MS Windows by default and easy to configure and cheaper. But if you’re dealing with sensitive information, it is not secured enough as it doesn’t require Public Key Infrastructure (PKI) to run, which uses digital certificates for authentication.
OEMs: Sophos, Barracuda, GFI
Network Access Control (NAC)
Providing a seamless experience for today’s mobile users with laptop, smartphone and fast adoption of IoT devices has increased network vulnerabilities and operational burden. With most data breaches starting at end-points, you need granular control over users, consistent policies, centralized in-depth visibility and control over all end-points across your wired and wireless networks.
Using NAC solution, you can accelerate troubleshooting by separating network from application issues and avoid service disruptions with pro-active performance monitoring and alerts. NAC was deployed to assist with BYOD (Bring-Your-Own-Device) policies and is now getting renewed focus as a means to safely accommodate IoT devices in the network.
Many of today’s security breaches have been due to compromised user accounts and passwords with inappropriate levels of access. Identity and Access Management solution provides the necessary services to securely confirm the identity of users and devices as they enter the network.
Centralized authentication services includes single sign on(SSO) services, certificate management, eToken and guest management. eToken further confirms the identity of users by adding a second factor to the authentication process through physical and mobile application based tokens.
OEMs: Aruba, Extreme Networks
Endpoint Data Protection
With more than 70% of corporate data residing on desktops/laptops – the desktop management has become a never-ending job for the IT dept. With increasing service requests and growth in the number of desktops – overall time spent towards this repetitive nature of work- kills the productivity of IT team.
Server or appliance based centralized deployment, ease of installation & configuration, light weight & performance optimised, granular report and post installation support–are the key factors of choosing the right solution.
 DLP & Encryption
DLP & Encryption
Data leakage prevention solution with user Identity-based policies helps to protect sensitive corporate data, preserve customer data privacy and meet regulatory compliance and security requirements while retaining work flexibility. Network security appliances offer gateway data leakage prevention controlling data transfer over email, web mail, file upload and file transfer applications.
Email Leakage Prevention – Organizations have to implement Identity-based policies to block attachments and forward email copies of departing and pre-specified employees to their managers and IT security. The result is quick preventive action against data leakage. Email archiving prevents destruction of critical data.
Web Leakage Prevention – Firewall prevents file upload over HTTP, Web mail, FTP, P2P and other file sharing applications based on username and work profile.
Instant Messenger Leakage Prevention – Firewall can be configured to block chat conversations based on pre-specified keywords and file transfer over IM in accordance with Identity-based policies.
Encrypted HTTPS/SSL Protocol Leakage Prevention – Cyberoam controls file upload over HTTPS/SSL websites, preventing misuse of this encrypted medium in the form of unauthorized transfer of sensitive data.
Logging and Reporting – Identity-based logging and reporting includes chat logs which help in monitoring and taking corrective action. The extensive logs and reports support CIPA, HIPAA, PCI DSS regulatory compliance.
